How to use it? @ Threat Zone — Network Analysis

What is Network Analysis for Malware ?
Analysis is the process of inspecting malware samples to learn more about their nature, functionality, and purpose. This, in turn, generates a signature that can be stored in a database to protect other users from infection.
Why is important?
Signature-based malware detection is used to identify malware that is already “known.” The signature-based methodology does not recognize new versions or mutations of malware.95% of malware files analyzed evolved within a 24-hour period or less. Advanced malware can change their signatures to avoid detection using a variety of transformation techniques such as code permutation, register renaming, expanding and shrinking code, and the insertion of garbage code, among others.
When we need to use it?
Network analysis can refer to a variety of things, but it almost always refers to malicious network activities that go beyond what is considered normal. Despite the fact that this explanation is somewhat general, such behavior will appear to have more distinct characteristics depending on the vulnerability exploited or the type of malware discovered.
How do I use it at Threat.Zone?
Network Analysis features and explanations used in the file can be found in the Dynamic Scan Report of the file you’re looking at in Threat Zone.
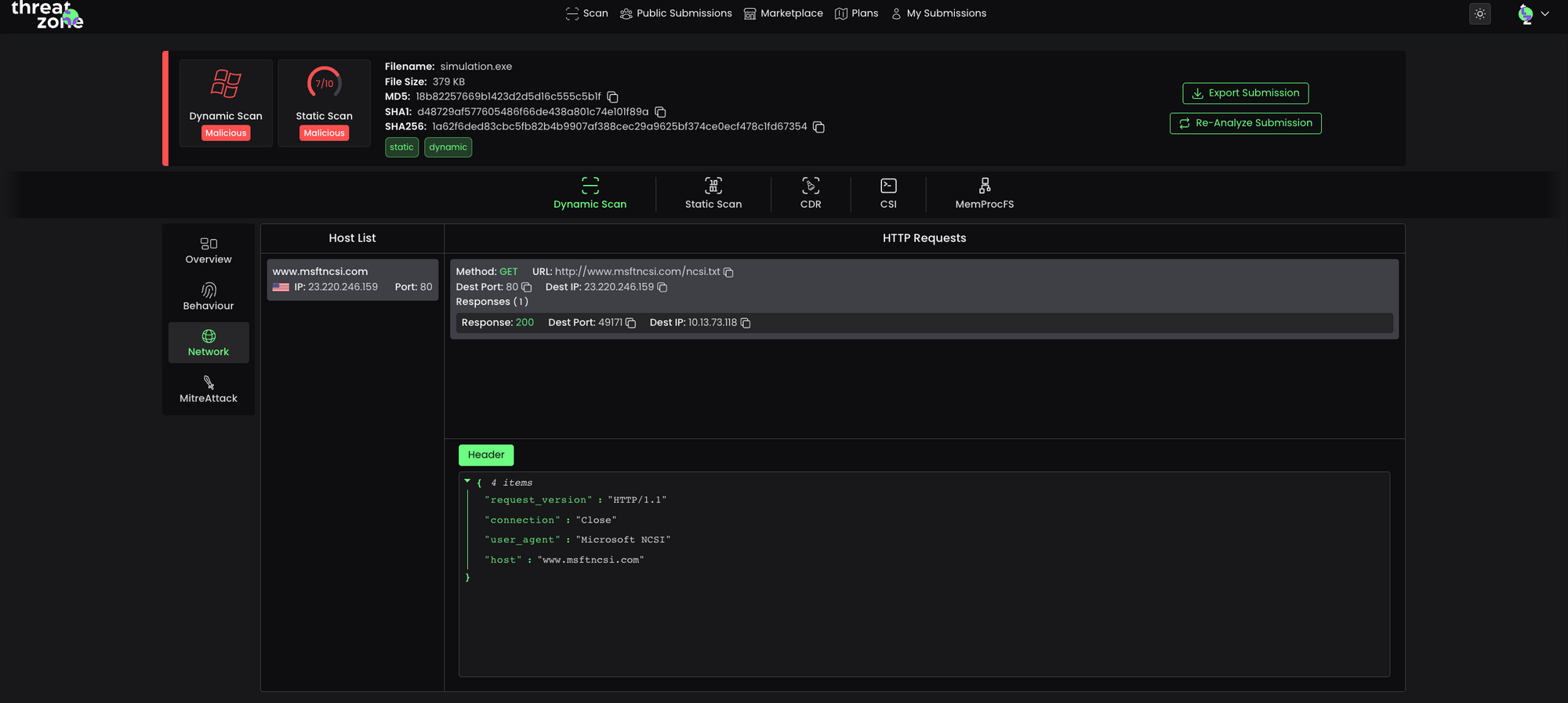
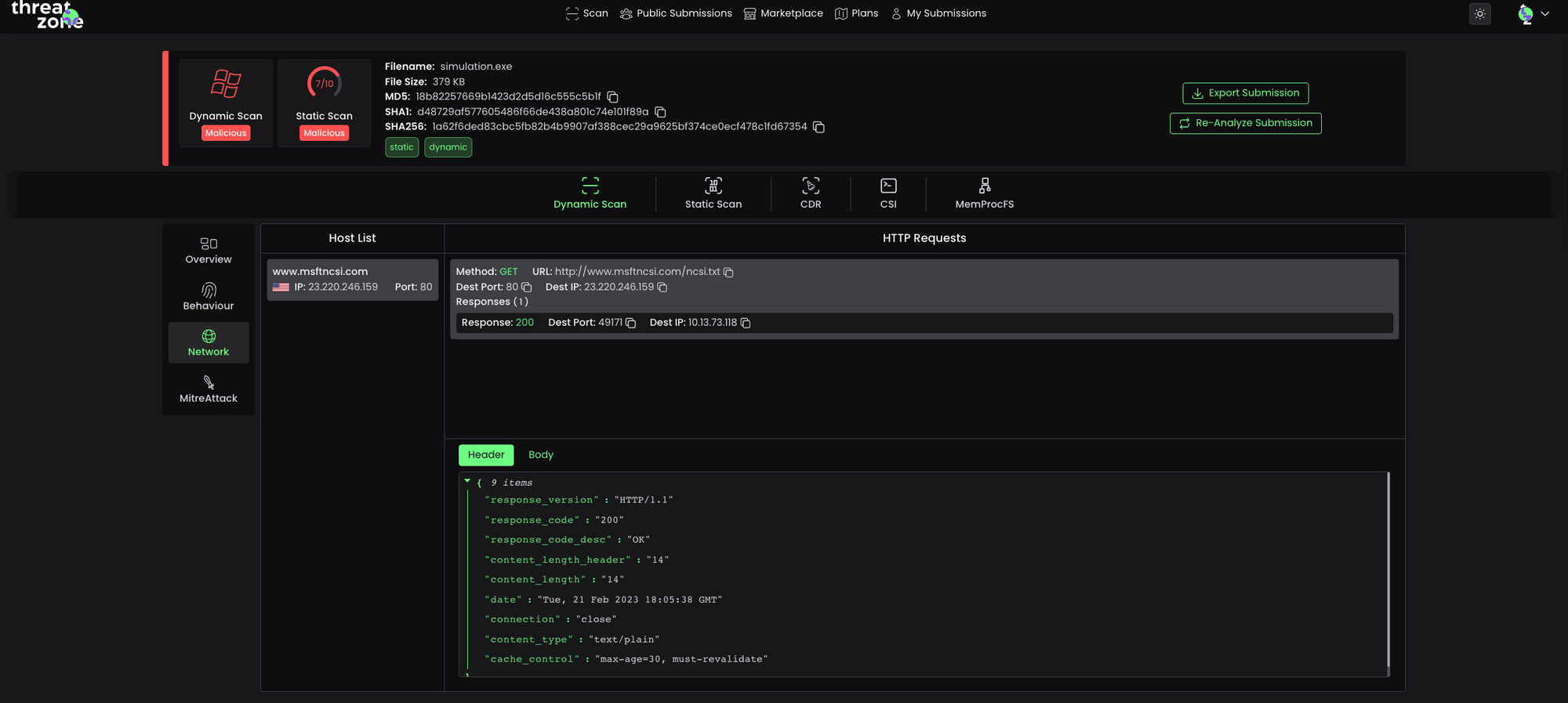
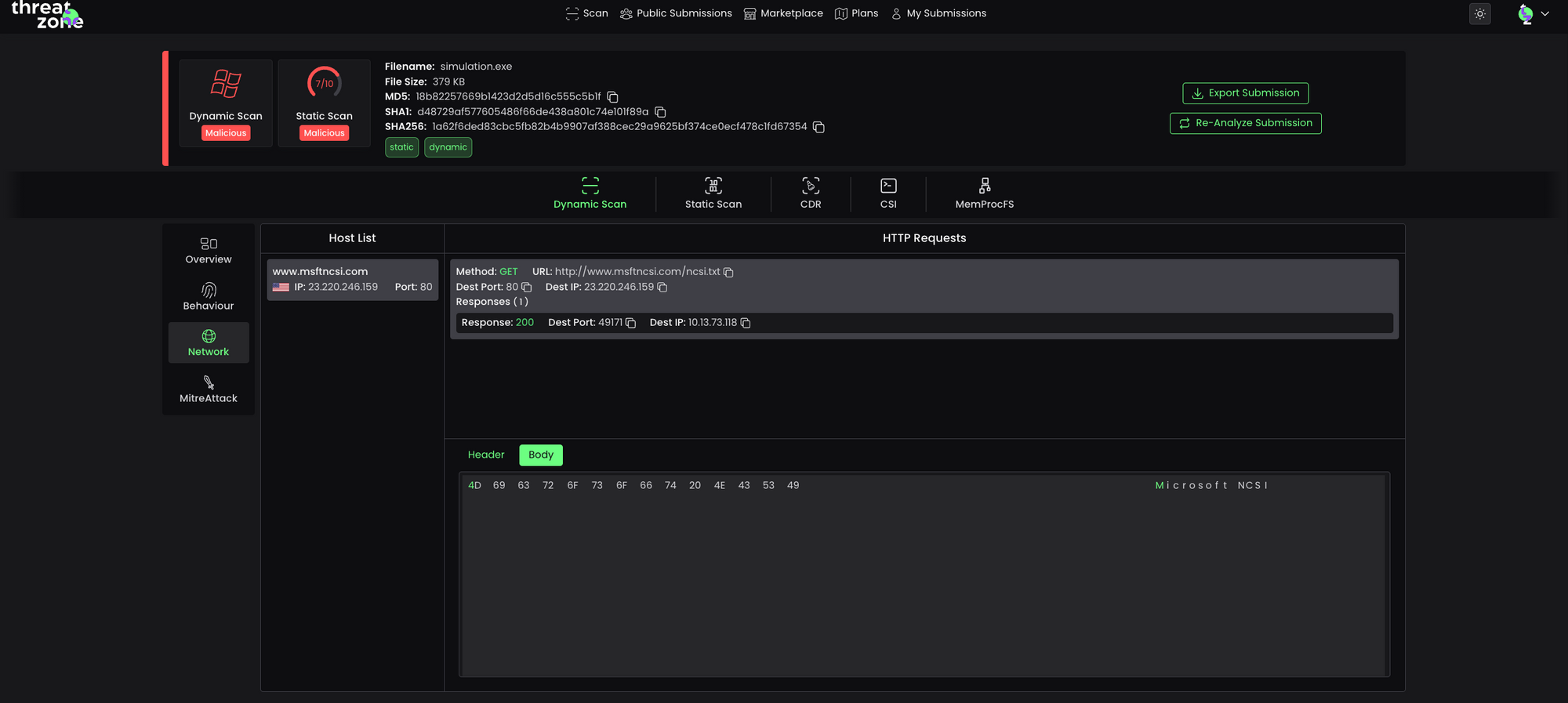
To see an amazing malware sandbox 👉 https://threat.zone/
Follow us on Twitter and Linkedin 👇

